Cybersecurity experts are raising alarms over a new phishing-as-a-service (PhaaS) toolkit named Rockstar 2FA, designed to steal Microsoft 365 credentials through adversary-in-the-middle (AiTM) attacks. This sophisticated toolkit enables attackers to bypass multi-factor authentication (MFA) by capturing both user credentials and session cookies.
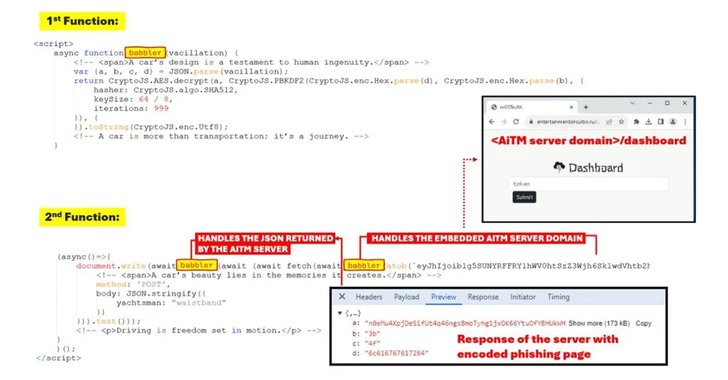
According to Trustwave researchers Diana Solomon and John Kevin Adriano, “Even users with MFA enabled are not immune, as the AiTM attack intercepts session cookies, granting attackers unauthorized access.”
An Evolution of the DadSec Phishing Kit
Rockstar 2FA is believed to be an enhanced version of the DadSec (aka Phoenix) phishing kit, with Microsoft tracking the developers under the alias Storm-1575. This toolkit is marketed on platforms like ICQ, Telegram, and Mail.ru under a subscription model, priced at $200 for two weeks or $350 for a month. Its accessibility makes it a preferred choice for cybercriminals with minimal technical skills.
Prominent features of Rockstar 2FA include:
- MFA bypass and session cookie theft
- Antibot protection with Cloudflare Turnstile
- Customizable login page themes resembling popular platforms
- Telegram bot integration for campaign management
- Fully undetectable (FUD) phishing links
A modern admin panel further allows threat actors to manage phishing campaigns, generate URLs, and track real-time status.
Sophisticated Phishing Tactics
Trustwave reports that attackers use diverse strategies, such as embedding URLs, QR codes, or document attachments in emails sent from compromised accounts. The phishing emails are often disguised as file-sharing notifications or e-signature requests, employing legitimate link redirectors like Atlassian Confluence, Google Docs Viewer, LiveAgent, and Microsoft OneDrive to evade detection.
The phishing pages are crafted to mimic genuine Microsoft sign-in portals. Once users enter their credentials, the data is instantly exfiltrated to the attacker-controlled server. These credentials, combined with session cookies, grant attackers persistent access to the victim’s account.
Broader Phishing Campaigns
In a related discovery, Malwarebytes has uncovered a phishing campaign named Beluga, which uses .HTM attachments to lure victims into providing their Microsoft OneDrive credentials on fake login pages. The stolen credentials are subsequently forwarded to a Telegram bot.
Adding to the concern, deceptive phishing ads and malicious apps like MobiDash have surfaced on social media, stealing financial and personal information. Victims lured by fraudulent betting apps have reported significant losses, with some exceeding $10,000.
Implications for Cybersecurity
The increasing sophistication of phishing-as-a-service platforms like Rockstar 2FA underscores the need for heightened awareness and advanced defensive measures. Businesses and individuals are urged to adopt robust email security solutions, stay cautious of unsolicited emails, and enforce strong multi-layered authentication systems.