A recent study has highlighted critical security vulnerabilities in multiple tunneling protocols, exposing 4.2 million hosts, including VPN servers, routers, and mobile network gateways, to potential cyberattacks. Conducted by Top10VPN in collaboration with Mathy Vanhoef, a professor and researcher from KU Leuven, the research warns of significant risks stemming from inadequately secured tunneling protocols.
“Internet hosts that accept tunneling packets without verifying the sender’s identity can be hijacked to perform anonymous attacks and provide unauthorized access to their networks,” Top10VPN reported.
The study found that millions of hosts, such as VPN servers, ISP home routers, core internet routers, content delivery network (CDN) nodes, and mobile network gateways, are susceptible to exploitation. The most affected countries include China, France, Japan, the United States, and Brazil.
Attack Mechanisms and Potential Impacts
The vulnerabilities identified could enable attackers to abuse affected systems for various malicious activities. These include using the systems as one-way proxies, spoofing source IPv4/6 addresses, and executing denial-of-service (DoS) attacks. According to an advisory from the CERT Coordination Center (CERT/CC), such vulnerabilities could also allow adversaries to infiltrate an organization’s private network or leverage vulnerable systems to conduct distributed denial-of-service (DDoS) attacks.
“An adversary can exploit these security flaws to create one-way proxies and spoof IP addresses, bypassing network filters and gaining unauthorized access to sensitive networks,” CERT/CC emphasized.
Root Causes of Vulnerabilities
The primary issue lies in the tunneling protocols—such as IP6IP6, GRE6, 4in6, and 6in4—which are designed to facilitate data transfers between disconnected networks. These protocols lack built-in mechanisms for authentication and encryption, making them vulnerable to malicious traffic injection when not paired with robust security measures like Internet Protocol Security (IPsec).
This flaw is not entirely new. A similar vulnerability was flagged in 2020 under the CVE-2020-10136 identifier. The recent study assigns new CVE identifiers to the vulnerabilities in question:
- CVE-2024-7595 – GRE and GRE6
- CVE-2024-7596 – Generic UDP Encapsulation
- CVE-2025-23018 – IPv4-in-IPv6 and IPv6-in-IPv6
- CVE-2025-23019 – IPv6-in-IPv4
Exploitation Methodology
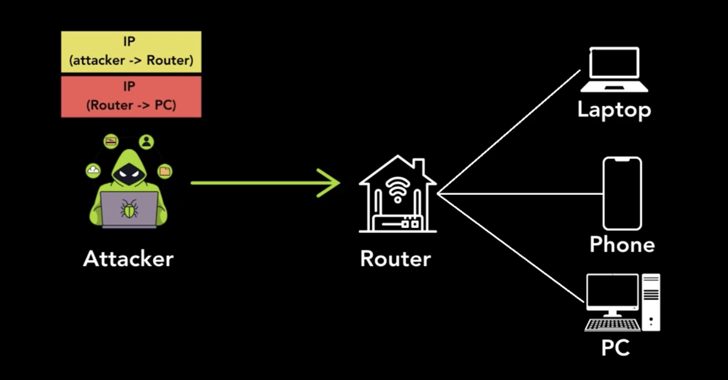
Simon Migliano of Top10VPN explained the exploitation process: “An attacker only needs to send a packet encapsulated using one of the affected protocols with two IP headers. The outer header contains the attacker’s source IP with the vulnerable host’s IP as the destination. The inner header’s source IP is that of the vulnerable host, while the destination IP is the target of the attack.”
Upon receiving such a malicious packet, the vulnerable host automatically removes the outer IP header and forwards the inner packet to its intended destination. Because the source IP address on the inner packet matches that of the trusted host, it easily bypasses network filters, enabling attackers to exploit the system for anonymous and potentially destructive actions.
Recommended Mitigation Measures
To mitigate these vulnerabilities, experts recommend implementing robust security protocols. Some of the key defenses include:
- Using IPsec or WireGuard: These protocols provide essential authentication and encryption, ensuring the integrity of tunneling packets.
- Restricting Packet Acceptance: Only accept tunneling packets from trusted and verified sources to minimize exposure.
- Traffic Filtering: Deploy traffic filtering measures on routers and middleboxes to block unauthorized or malicious traffic.
- Deep Packet Inspection (DPI): Utilize DPI techniques to analyze and filter tunneling packets more effectively.
- Blocking Unencrypted Tunneling Packets: Ensure that all tunneling traffic is encrypted and authenticated to prevent malicious exploitation.
Broader Implications
The potential impact of these vulnerabilities is far-reaching. Victims of DoS attacks may experience network congestion, service disruptions, and even crashes of overloaded network devices. Additionally, attackers could exploit these flaws to carry out man-in-the-middle attacks and intercept sensitive data.
“The consequences for victims include network congestion, service interruptions, and resource exhaustion caused by traffic overload. In severe cases, these attacks could lead to device crashes and open avenues for further exploitation,” Migliano cautioned.
The study underscores the need for organizations and individuals to proactively secure their systems against such vulnerabilities. Given the critical role of tunneling protocols in modern networking, ensuring robust security measures is imperative to protect against evolving cyber threats.